The Threat of Linux Bootkits
Recently, security researchers have been analyzing and publishing details about “Iranukit” and “Bootkitty,” malware that targets Linux systems with bootkits. Bootkitty has been getting media coverage and is touted as the first UEFI bootkit for Linux. ESET’s research team created a post detailing the analysis of Bootkitty and, on December 2, 2024, made the following update:
“UPDATE (December 2nd, 2024): The bootkit described in this report seems to be part of a project created by cybersecurity students participating in Korea’s Best of the Best (BoB) training program. As they informed us: “The primary aim of this project is to raise awareness within the security community about potential risks and to encourage proactive measures to prevent similar threats. Unfortunately, few bootkit samples were disclosed prior to the planned conference presentation.“
(Reference: Bootkitty: Analyzing the first UEFI bootkit for Linux)
We should continue to analyze the malware made public and implement detections for this type of threat, despite it being a PoC creation and not being observed being used in the wild by actual threat actors against actual targets. As we’ve seen with threats such as BlackLotus, malware, and specific “new” techniques, they can start as observed in development and quickly progress to being observed and used by threat actors.
While Bootkitty does exemplify some “new” behaviors and techniques, the various components are attacks we have observed before. Before the widespread adoption of UEFI (and Secure Boot), attackers created bootkits and malware that infected the MBR. In 2013, researchers from Quakerslabs presented Dreamboot, a UEFI bootkit concept that could be applied to various operating systems (including Linux). Other bootkits have been documented as well, including QuarkMatter (CIA circa 2016 via Wikileaks) and FinSpy’s UEFI bootkit component that dates back to 2014 (We also wrote about Finspy’s UEFI and MBR Bootkit).
In addition to discussing some of the capabilities of Bootkitty, we will discuss ways the Eclypsium Platform can help detect this type of threat, specifically:
- Detection of the LogoFAIL vulnerability across several platforms
- Alerting on baseline changes to core Linux components, such as bootloaders
- Rules for detection of Linux malware behavior observed in the published samples labeled “Iranukit” and “Bootkitty”
Separating Components and Functionality
There were two samples recently analyzed by security researchers:
- Independent security researcher Humzak711 analyzed the Linux userland components in a malware kit called Iranukit. The samples included a weaponized LogoFAIL capability.
- ESET analyzed the “Bootkitty” malware sample
After reviewing the various write-ups, it was clear that Bootkitty itself would not bypass Secure Boot as it used self-signed certificates. However, pairing the Bootkitty bootkit with the LogoFAILl UEFI vulnerabilities and exploits allows the attacker to feed in certificates that will allow Bootkitty to execute. LogoFAIL was exploited to allow an attacker to add a MOK (Machine Owner Key) that allows the backdoored bootloader and kernel to pass Secure Boot verification. This process is done without the user interaction required when adding a MOK (typically a passphrase is required during the MOK installation from the operating system, then the system is rebooted, the passphrase is entered, and the key is accepted and added).
Terminology Note
When reading about this type of threat (and techniques), it is common to see the following terms confused with each other:
UEFI Implant – A UEFI implant is malware that infects the Unified Extensible Firmware Interface, the modern successor to BIOS. It runs before the operating system loads, allowing attackers to maintain persistence, compromise OS integrity, and evade most security controls.
Bootkit – A bootkit is malware designed to infect a computer’s bootloader or boot process, executing malicious code before the operating system initializes. By targeting the pre-boot environment, bootkits can bypass standard security measures and remain hidden, often surviving OS reinstallations (but far easier to recover from than a UEFI implant).
Rootkit – A rootkit is a program that provides continued privileged access to a computer while actively hiding its presence (typically in the kernel or userland). It allows an attacker to maintain command and control over a system without the owner’s knowledge, enabling remote file execution, system configuration changes, and spying on user activities.
Secure Boot bypasses allow GRUB-based bootkits to be installed on the system. In this case, the malicious code does not persist in UEFI, which means the user can swap back a known-good bootloader to recover from an infection. Many references to this attack will point out that systems vulnerable to LogoFAIL are the targets, and it is recommended that this vulnerability be remedied. While systems administrators should apply patches for the LogoFAIL vulnerabilities, many other UEFI vulnerabilities and Secure Boot bypasses exist that could also be used to successfully deploy bootkits such as Bootkitty (You can find several more Secure Boot bypass techniques here). Also, many Linux users and Linux systems administrators do not enable or configure Secure Boot as implementations vary across distributions and environments, making it possible to carry out this attack without Secure Boot getting in the way.
The userland malware from Iranukit consists of several components working together to achieve stealth and persistence, including a shared object file, two kernel modules, and two binary executables. The rootkit components employ techniques to hide files, processes, and network traffic, such as manipulating kernel module lists and hooking system calls. IranuKit’s modular design and placeholder functions suggest ongoing development, with some components showing low detection rates on VirusTotal. The analysis reveals a complex chain of operations, from loading kernel modules to unpacking and executing binaries, demonstrating the rootkit’s capabilities in evading detection and maintaining a foothold on infected systems.
Detection
Attackers employing Linux bootkits in the manner described above can be detected by tracking changes to bootloaders on the system. Typically, the bootloader on a system will only change as part of a system update. If the bootloader changes, either the EFI file itself or a completely new EFI program is swapped out, independent of a system update a security alert should be raised. Using the Eclypsium Platform, we can:
- Set a baseline for bootloaders, marking existing bootloaders as the known good binaries.
- Monitor the baseline for any changes that may occur to bootloaders
- Alert when the baseline changes for bootloaders on your systems
Below, you can see the alert details that will trigger when a baseline deviation is detected:
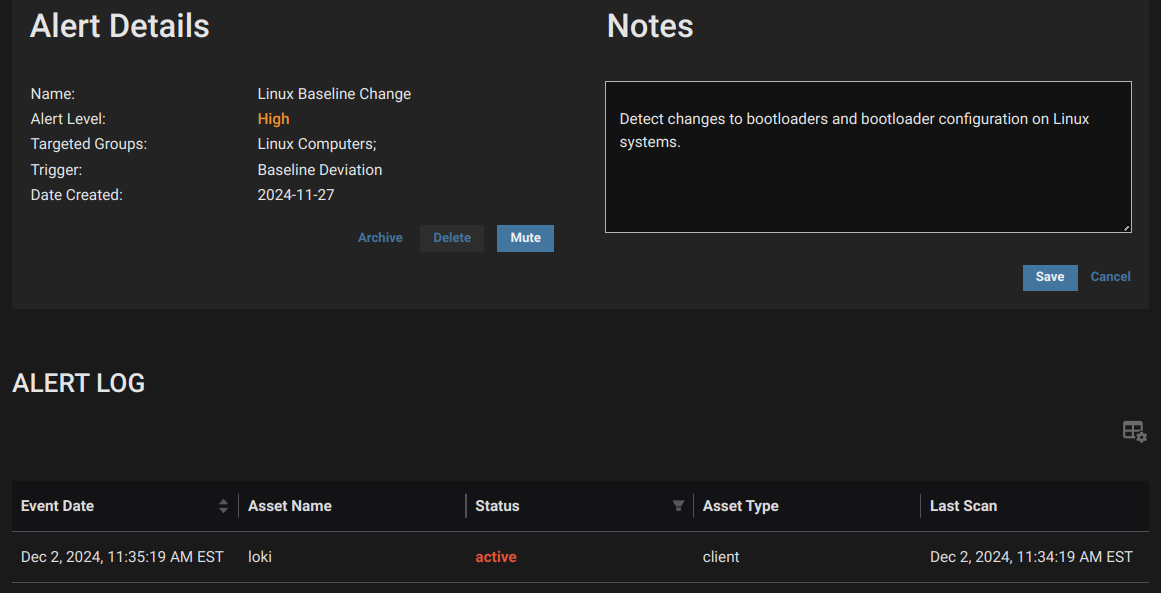
The host above has triggered this alert, noting that a change has been detected. If we dig into the details a bit more, we can see the alert was triggered via the Bootloader Scan History:
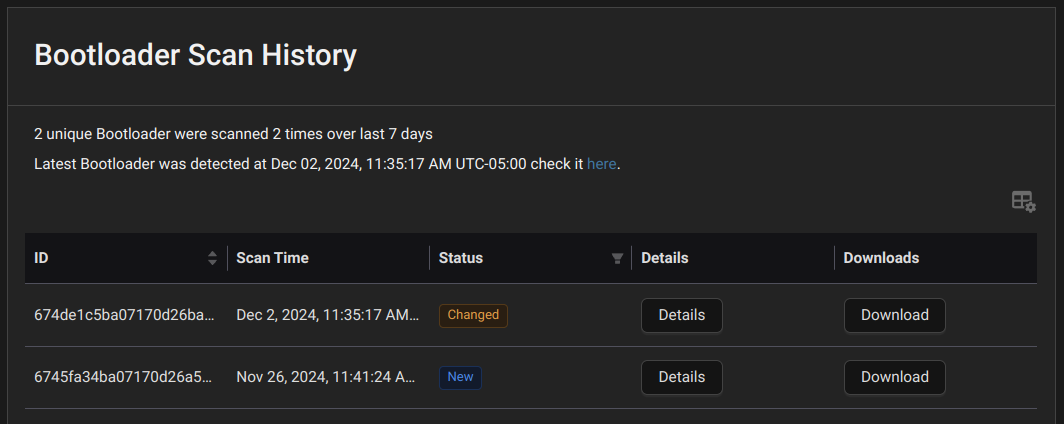
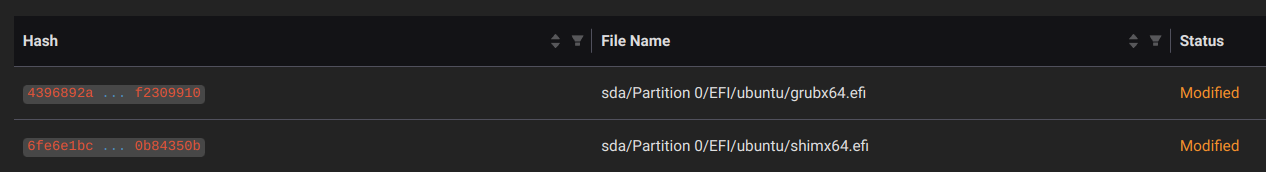
Digging into the details, we can see the hashes and associated files that have been modified. In this case, both shim and GRUB have changed:
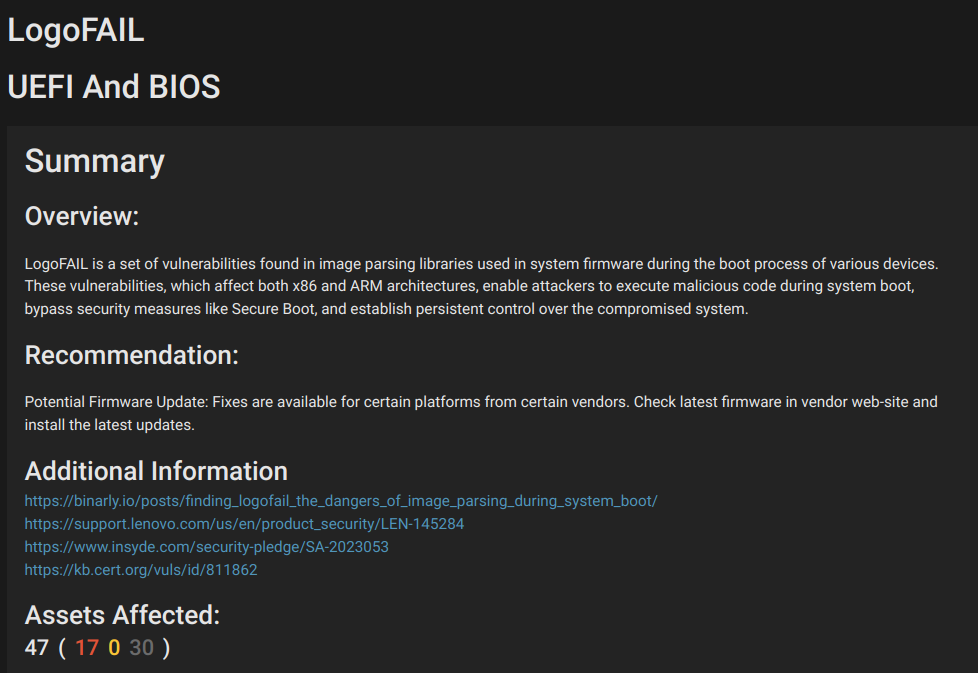
The Eclypsium Platform can also detect if a system is vulnerable to LogoFAIL:

Enhanced Detection
The Eclypsium Platform can now detect the techniques employed by bootkits and rootkits in UEFI and the Linux kernel by performing deep binary analysis. The binary analysis allows the platform to detect future bootkits and rootkits using similar techniques by identifying certain behaviors and characteristics indicative of malicious intent. Recently, we’ve added two new detection techniques:
- In UEFI, we can detect a new type of hooking mechanism
- In the Linux kernel, we detect many IoCs, such as suspicious kernel API calls
Summary
The emergence of Linux bootkits like Bootkitty, while initially concerning, serves as a valuable reminder of the evolving threat landscape in cybersecurity. Although Bootkitty turned out to be a student project, it highlights the potential risks and the need for proactive measures against similar threats in the future. The Eclypsium Platform offers robust detection capabilities, including monitoring bootloader changes, identifying systems vulnerable to LogoFAIL, and employing enhanced techniques to detect malicious behaviors in UEFI and the Linux kernel. As the threat landscape evolves, organizations must remain vigilant and implement comprehensive security measures that address vulnerabilities at all levels, from firmware to the operating system. By staying informed about emerging threats and leveraging advanced detection tools, we can better protect our systems against sophisticated attacks that target the very foundations of our computing infrastructure.
References:
- Bootkitty: Analyzing the first UEFI bootkit for Linux
- Found on VirusTotal: The world’s first UEFI bootkit for Linux
- Code found online exploits LogoFAIL to install Bootkitty Linux backdoor
- Analyzing IranuKit: A modular linux kernel rootkit
Historical Bootkit References:
- There’s a Hole in the Boot (Eclypsium researchers Mickey Shkatov and Jesse Michael in 2020)
- Bootkit: the challenge of 2008
- VB2014 paper: Bootkits: past, present & future
- ESET White Paper: Mind the Gapz (2013)
- UEFI and Dreamboot (HiTB 2013 – Quarkslabs)






