IT security teams are assessing new UEFI vulnerabilities that affect Windows and Linux systems. The vulnerabilities are collectively called LogoFAIL because they exist in UEFI image parsers that display the manufacturer logo when the system boots up.
Affected vendors include UEFI suppliers AMI, Insyde, and Phoenix and device manufacturers such as Lenovo, Dell, and HP. Some vendors have already issued advisories, but we should expect the list to expand as more vendors assess their exposure.
While we are not aware of exploitation in the wild, Eclypsium customers will be able to detect the vulnerabilities as well as indicators of potential exploits of the LogoFAIL vulnerabilities with the version 3.4 release. Eclypsium can also assist in the remediation process by identifying vulnerable components and automating firmware updates.
LogoFAIL Summary
Exploiting LogoFAIL vulnerabilities requires attackers to replace the logo image with a malicious look-alike that includes specially crafted code to exploit vulnerabilities in the UEFI image parsers. Because the exploitation occurs in the Driver Execution Environment (DXE), a very early stage of the boot process, it can bypass built-in security protections such as Secure Boot. Attackers can run arbitrary code before the operating system and any endpoint security agents that might be installed on the device.
LogoFAIL CVEs and Severity Scores
Defenders need to know which systems are affected by LogoFAIL vulnerabilities and the associated severity. The CERT Coordination Center at Carnegie Mellon has a dynamic list of affected vendors and associated security advisories.
So far, it is difficult to determine the severity as no public exploit has been published, and some of the now public vulnerabilities have been scored differently by the researchers from Binarly who discovered the LogoFAIL vulnerabilities, the UEFI firmware vendors (Phoenix Technologies, Insyde, and AMI), and the National Vulnerability Database (NVD). The severity and exploitability of each LogoFAIL vulnerability will likely depend on how affected firmware vendors and equipment manufacturers (OEMs) store and process logo images. An attacker’s ability to modify these logo images or paths to them may depend on malicious software running locally on a system (with administrative or root-level privileges), by an attacker remotely accessing the system, or by an attacker who gained physical access to a target.
You should monitor and apply patches as they become available from each OEM for each product model. As of the time of this writing, the list of affected products that have associated CVE identifiers includes the following:
Insyde
Insyde has issued INSYDE-SA-2023053 and assigned it a CVSS score of 4.4. The associated CVE is CVE-2023-40238 and has been scored a CVSS 5.5 (Medium) by the NVD. The aforementioned CVE correlates to Binarly’s vulnerability identifier BRLY-LOGOFAIL-2023-006 with an assigned CVSS of 8.2 (High). The difference in CVSS score appears to result from differences in perceived potential impact on confidentiality, integrity, and availability.
AMI
AMI has issued AMI-SA-2023009 and assigned a score of 7.5 to each of the associated CVEs, while the NVD has assigned a score of 7.8:
- CVE-2023-39538 – AMI CVSS = 7.5 (High), NVD CVSS = 7.8 (High)
- CVE-2023-39539 – AMI CVSS = 7.5 (High), NVD CVSS = 7.8 (High)
The severity rating for the AMI vulnerabilities is higher than the CVE in Insyde firmware due to stated impact on confidentiality and integrity.
Phoenix Technologies
Phoenix Technologies has released an advisory and the associated CVE (CVE-2023-5058) has been issued. At the time of this writing, no CVSS scores have been provided.
While Phoenix has encouraged customers to upgrade to the latest version of firmware, it is unclear when patches from all vendors will be available to customers.
Detection and Recommendations
LogoFAIL represents a class of vulnerabilities in image parsing functionality of UEFI firmware in Windows and Linux systems. While firmware vendors have issued advisories, the scope of the impact and severity of these vulnerabilities on various systems will become clear as more affected OEMs publish advisories and release updates. It’s important to look for new advisories and plan to install new updates as they are published by OEMs. In the meantime, Eclypsium has added detection of specific instances of LogoFAIL vulnerabilities affecting AMI, Phoenix Technologies, Insyde-based UEFI firmware on PC and server systems. We are also working on adding a capability to monitor systems for potential exploitation of the LogoFAIL class of vulnerabilities. As more advisories become available from OEMs and as proof-of-concept exploits become available we will be adding detection of both vulnerabilities and indicators of compromise/exploitation.
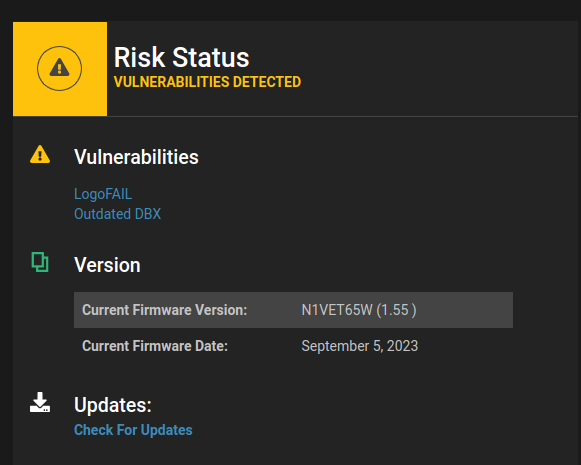
Eclypsium customers who are configured to use the Automated Firmware Update capability will start receiving notifications about the new firmware updates as they are published by OEMs, verified, tested, and added to the Eclypsium platform.
Keep up to date with threats to low-level components such as UEFI by subscribing to our newsletter.