F5 recently disclosed that a nation-state actor accessed a proprietary BIG-IP development network, including source code and details about vulnerabilities still under development. Bloomberg reported that the company sent customers a threat hunting guide for the “Brickstorm” malware, linked by Mandiant to UNC5221—a China-based state-sponsored group known for stealing source code from major tech providers.
In response, CISA has released Emergency Directive 26-01 mandating that federal agencies inventory and patch all BIG-IP hardware, as well as all instances of BIG-IP F5OS, BIG-IP TMOS, Virtual Edition (VE), BIG-IP Next, BIG-IQ software, and BNK/CNF. End of service BIG-IP devices must be decommissioned.
While F5 has found no evidence that the stolen vulnerabilities have been exploited, the source code exposure means all F5 customers—not just federal agencies—should treat their deployments as potentially compromised. F5 has released patches to address 44 vulnerabilities, including those in Big-IP.

Network Devices Are Undersecured and Increasingly Targeted
This disclosure adds momentum to the worrisome trend of cyberattackers targeting network edge devices and the IT supply chain to compromise high-profile targets. In Mandiant’s 2025 M-Trends Report, they noted that the most frequently exploited vulnerabilities affected Palo Alto and Ivanti network edge devices. The Verizon DBIR Report for 2025 stated an 8x increase in exploitation of vulnerabilities against network edge devices. Earlier in 2025, the U.S. National Guard revealed that their networks had been compromised by Salt Typhoon via their Cisco and Palo Alto Networks equipment. Just weeks ago, CISA issued another Emergency Directive (ED 25-03) focused on widely deployed Cisco ASA appliances.
In an investigation of the APT group UNC 3886, which targeted Juniper routers earlier this year, Mandiant noted a shift in the attack group’s tactics. Mandiant’s report stated that UNC 3886 was increasing their “focus on malware and capabilities that enable them to operate on network and edge devices, which typically lack security monitoring and detection solutions, such as endpoint detection and response (EDR) agents.”
Adversaries are targeting these devices because it works.
Do Not Trust The Network Device Supply Chain
F5 has stated that they “have no evidence of modification to our software supply chain, including our source code and our build and release pipelines.”
Nonetheless, for F5 customers, it is hard to interpret this incident as anything other than a supply chain compromise. For those with dozens or hundreds of BIG-IP appliances deployed in their enterprise, the specter of undisclosed vulnerabilities having fallen into attackers’ hands requires urgent incident response.
The challenge of inventorying and patching all F5 technology and decommissioning End of Support assets will consume enormous amounts of time and energy from teams already stretched thin.
How Eclypsium Can Help Inventory and Secure F5 BIG-IP Systems
Eclypsium can detect the presence of vulnerable versions as well as the specific vulnerabilities disclosed by F5 as part of this security incident. Eclypsium can detect the BRICKSTORM backdoor, a malware associated with UNC-5221, a threat actor potentially responsible for the F5 security incident. Eclypsium offers deep visibility into F5 BIG-IP systems, including firmware versions, vulnerabilities, integrity changes, and other data, as seen in the image gallery below. Click to expand.
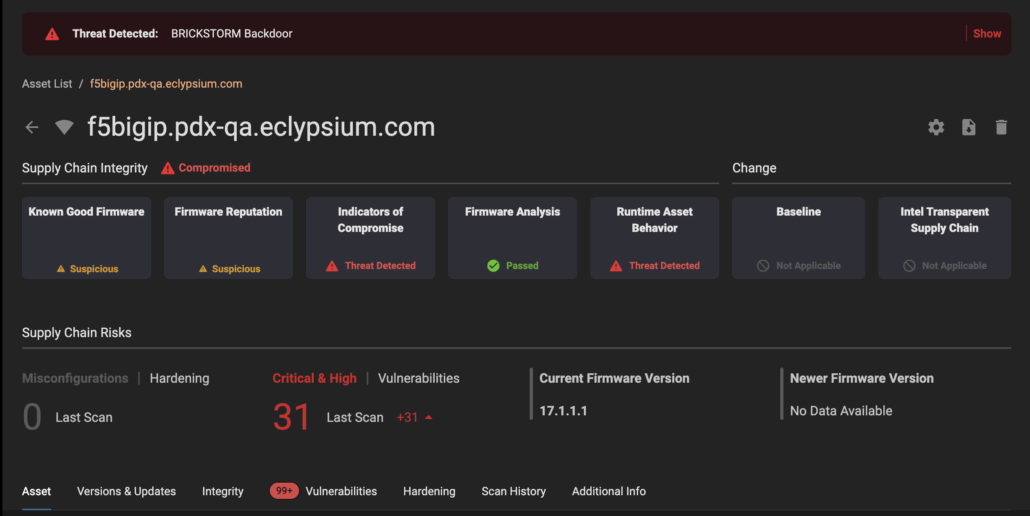
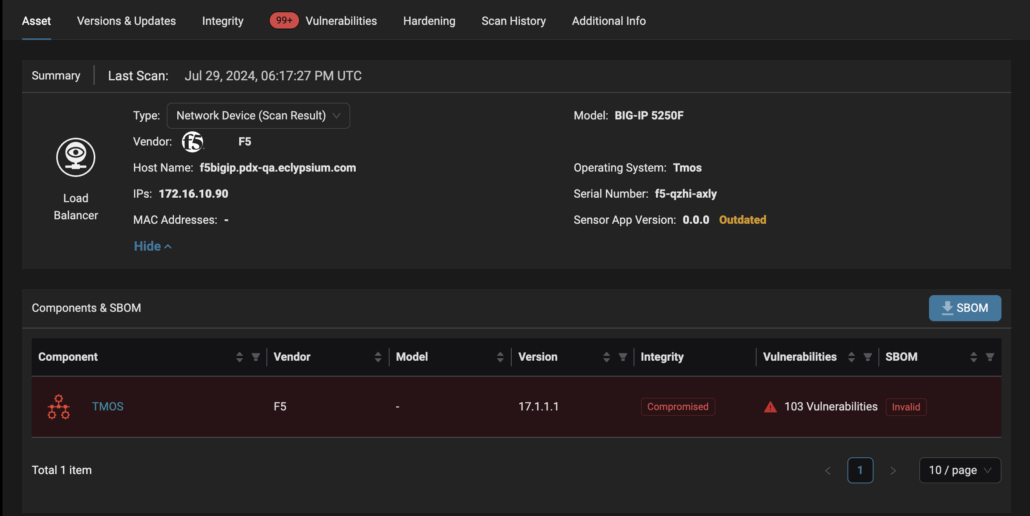
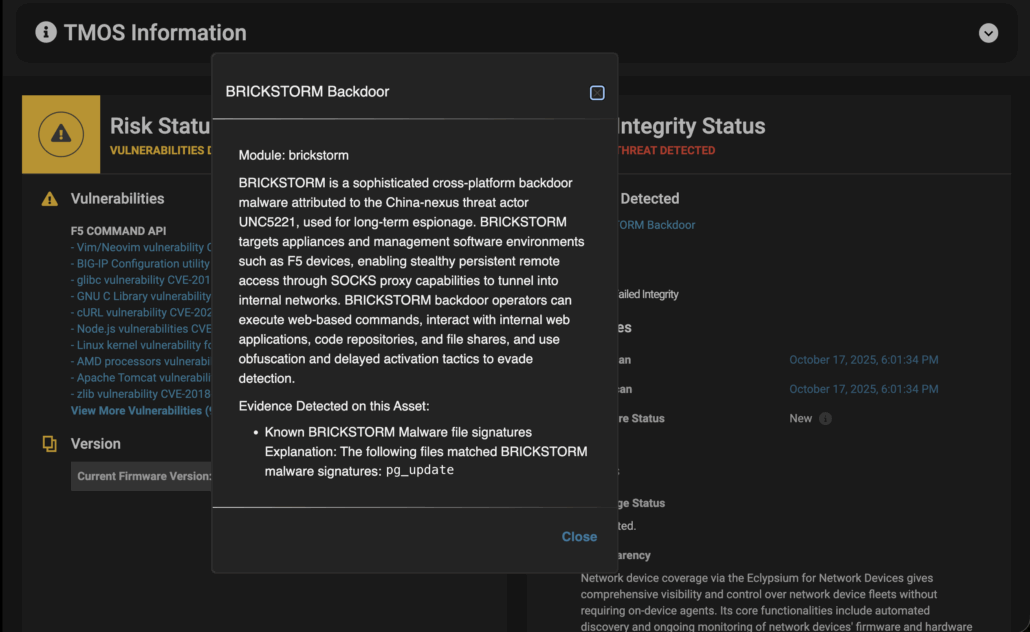
Eclypsium can also detect the 44 new vulnerabilities present in F5 BIG-IP technology disclosed as part of this incident, as well as other legacy vulnerabilities that have had new affected versions disclosed, and can monitor the integrity of F5 BIG-IP technology’s firmware over time.
For years, Eclypsium has specialized in network infrastructure protection, delivering threat detection and integrity checking for the firmware running inside network devices, including F5 BIG-IP, Cisco ASA, Palo Alto NGFWs, Ivanti VPNs, and more. Eclypsium researchers have been monitoring network devices for a while, previously discovered and disclosed remotely exploitable vulnerabilities in F5 BIG-IP Next systems as well as exploits for BIG-IP as far back as 2022.
For organizations needing immediate support in inventorying and evaluating their BIG-IP footprint, Eclypsium can help discover and identify vulnerable systems and firmware versions, identify end of support (EOS) systems, roll out patches to affected systems and continuously monitor for threats as well as firmware integrity.
For existing customers, contact your Eclypsium account team to get started. Non-Eclypsium customers can contact us to get expert support in assessing and securing F5 environments.






