UEFIcanhazbufferoverflow: Widespread Impact from Vulnerability in Popular PC and Server Firmware
Summary
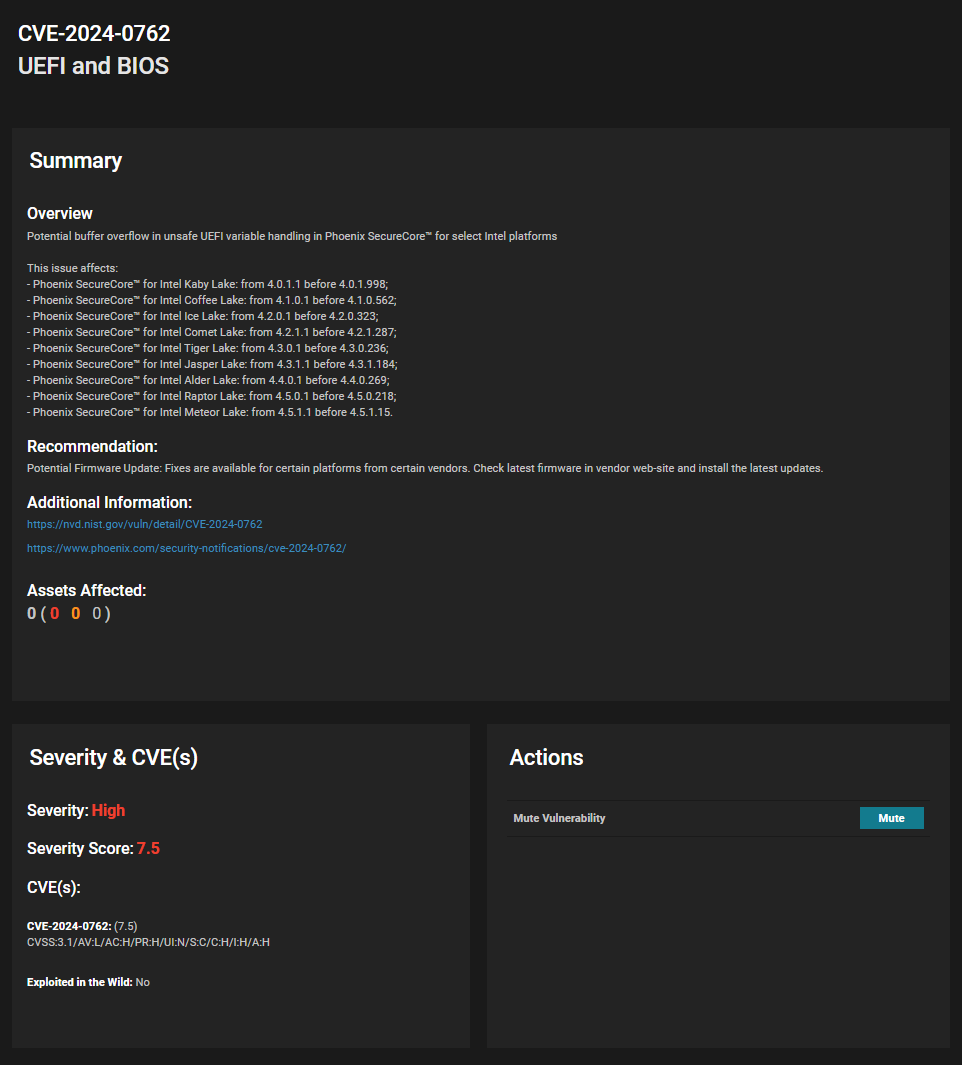
Eclypsium Automata, our automated binary analysis system, has identified a high impact vulnerability (CVE-2024-0762 with a reported CVSS of 7.5) in the Phoenix SecureCore UEFI firmware that runs on multiple families of Intel Core desktop and mobile processors. The issue involves an unsafe variable in the Trusted Platform Module (TPM) configuration that could lead to a buffer overflow and potential malicious code execution. To be clear, this vulnerability lies in the UEFI code handling TPM configuration—in other words, it doesn’t matter if you have a security chip like a TPM if the underlying code is flawed.
We originally identified the vulnerability on the Lenovo ThinkPad X1 Carbon 7th Gen and X1 Yoga 4th Gen, both using the latest Lenovo BIOS updates. However, Phoenix Technologies has subsequently acknowledged that the same issue applies to multiple versions of its SecureCore firmware that runs on Intel processor families including AlderLake, CoffeeLake, CometLake, IceLake, JasperLake, KabyLake, MeteorLake, RaptorLake, RocketLake, and TigerLake. These are Intel codenames for multiple generations of Intel Core mobile and desktop processors. Given that these Intel Core processors are used by a wide range of OEMs and ODMs, the same vulnerability could potentially affect a wide range of vendors and potentially hundreds of PC products that also use the Phoenix SecureCore UEFI firmware. The possibility of exploitation depends on the configuration and permission assigned to the TCG2_CONFIGURATION variable, which could be different for every platform.
The vulnerability allows a local attacker to escalate privileges and gain code execution within the UEFI firmware during runtime. This type of low-level exploitation is typical of firmware backdoors (e.g. BlackLotus) that are increasingly observed in the wild. Such implants give attackers ongoing persistence within a device and often, the ability to evade higher-level security measures running in the operating system and software layers. Additionally, the manipulation of runtime code can make attacks harder to detect via various firmware measurements.
This disclosure has been closely coordinated with Phoenix Technologies and Lenovo PSIRT. Lenovo has published relevant BIOS updates at Multi-vendor BIOS Security Vulnerabilities (May, 2024) – Lenovo Support US. Eclypsium customers can scan their devices to identify vulnerable assets in their environment. Customers should also refer to their relevant system manufacturer for guidance on affected devices and available updates.
Key Background
As the modern replacement for BIOS, UEFI is the all-important system firmware that controls how a device boots. UEFI also provides ongoing runtime management of the device below the OS via systems such as System Management Mode (SMM). As such UEFI is the first code to run and the most privileged on most any system.
These same traits have turned UEFI into a prime target for attackers with firmware implants and backdoors such as BlackLotus, CosmicStrand, and MosaicRegressor becoming increasingly common in the wild. These threats allow attackers to ensure that their malicious code can preempt and subvert the built-in protections and security tools that run in the OS and higher layers. This not only gives the attackers opportunity to cause damage, it also allows attackers to silently maintain persistence on a compromised device.
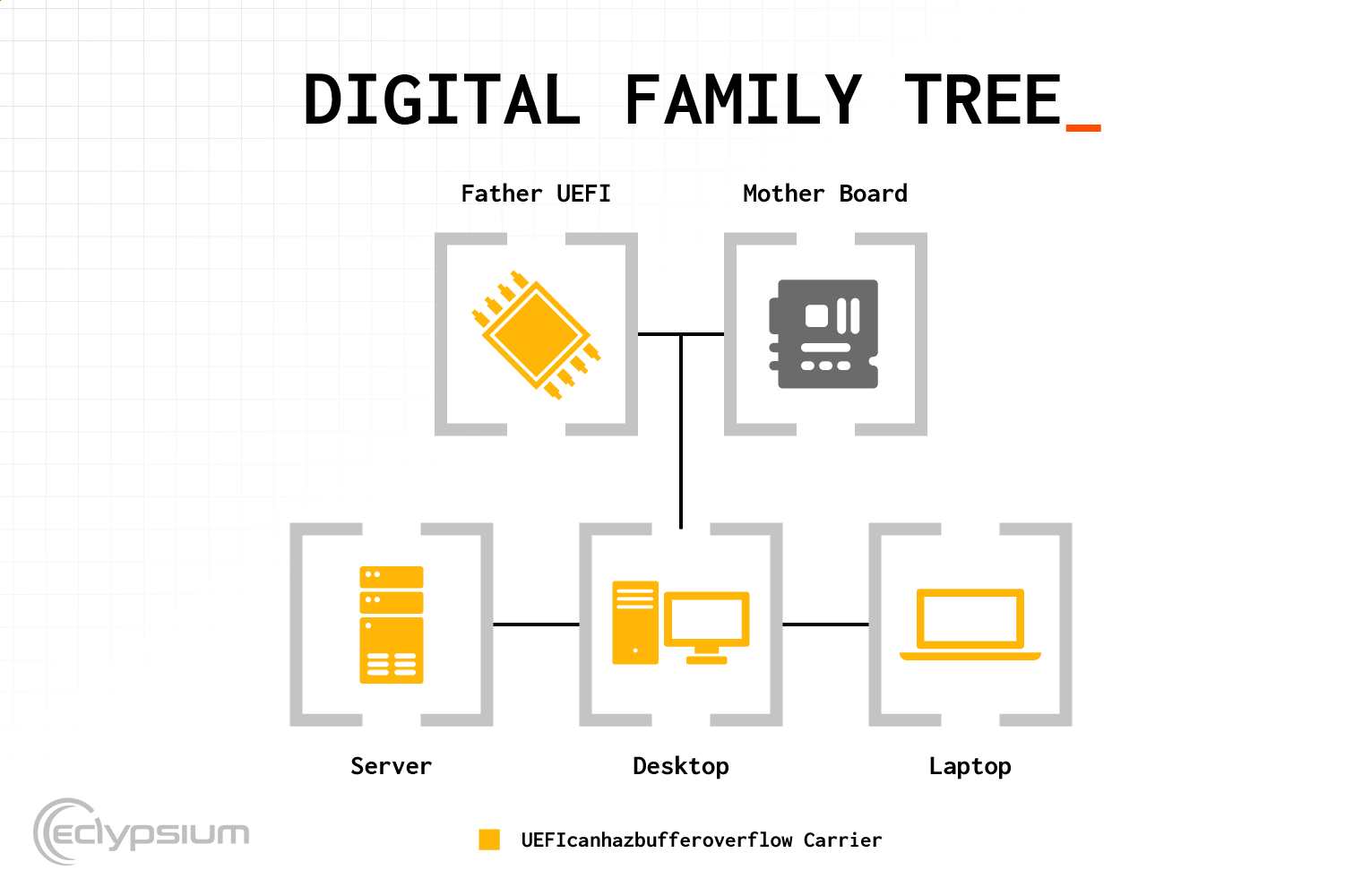
UEFI firmware also occupies a critical role in the technology supply chain. UEFI firmware development is a complex and specialized discipline and OEMs will often source their firmware from third-party firmware vendors. In this case, Lenovo licensed firmware from Phoenix Technologies, a well-respected and established firmware vendor. However, this also means that any vulnerabilities in an upstream supply-chain provider can potentially affect many different products and vendors. In this case, any manufacturer that uses versions of Phoenix firmware named in the CVE could be affected.
Vulnerability Details
This vulnerability was initially discovered by Automata, Eclypsium’s automated binary analysis system. Automata leverages the collective intelligence and experience of Eclypsium researchers and applies those insights and techniques at scale for production systems. It is worth noting that this vulnerability is similar to other UEFI vulnerabilities in HP devices that we have also recently reported on. However, these are distinct, separate vulnerabilities that were simply both discovered by Eclypsium Automata.
The vulnerability is related to the unsafe call to the GetVariable UEFI service.
Vulnerable module GUID: E6A7A1CE-5881-4B49-80BE-69C91811685C
There are two calls to GetVariable with the “TCG2_CONFIGURATION” argument and the same DataSize, without adequate checks in between. If an attacker can modify the value of the “TCG2_CONFIGURATION” UEFI variable at system run time, they can set it to a value long enough so that the first call to GetVariable returns EFI_BUFFER_TOO_SMALL, and the data_size is set to the length of the UEFI variable. The second call would succeed and overflow the buffer, leading to a stack buffer overflow.
void Function_0000537c(void){
...
ulonglong data_size;
char buffer [8];
...
EVar1 = (*gRS_2->GetVariable)
((CHAR16 *)TCG2_CONFIGURATION, &gTCG2_CONFIG_FORM_SET_GUID,
(UINT32 *)0x0, &data_size, buffer);
if (EVar1 == EFI_BUFFER_TOO_SMALL) {
EVar1 = (*gRS_2->GetVariable)
((CHAR16 *)TCG2_CONFIGURATION,&gTCG2_CONFIG_FORM_SET_GUID,
(UINT32 *)0x0,&data_size,buffer)
Phoenix has assigned CVE-2024-0762 to the vulnerability and addressed it on May 14, 2024. The CVSS 3.1 score is reported as 7.5 High. (CVSS:3.1/AV:L/AC:H/PR:H/UI:N/S:C/C:H/I:H/A:H)
Mitigations
As with other supply chain incidents, the first step of mitigation is to identify which devices are affected. Given that the vulnerability affects many Intel chipset families and Phoenix licenses firmware to many vendors, there are many potentially affected devices. As a result, Eclypsium customers are encouraged to scan their devices using the latest available version of the Eclypsium Platform, and search for any devices affected by CVE-2024-0762.
Once affected devices have been identified, customers should refer to the relevant vendor for firmware updates. At the time of writing, Lenovo has published the following firmware update:
Conclusion
This vulnerability exemplifies two characteristic traits of IT infrastructure supply chain incidents—high impact and broad reach. UEFI firmware is some of the most high-value code on modern devices, and any compromise of that code can give attackers full control and persistence on the device. And since the vulnerable code stems from a major supply chain partner that licenses code to multiple OEM vendors, the issue can potentially affect many different products.
To prepare for these types of incidents, enterprises must be able to independently assess devices and components using commercial tools like Eclypsium. IT and Security teams need the ability to know which assets contain which components, if any of those components are vulnerable, and ultimately if the integrity of an asset has been compromised. Eclypsium Automata ensures this can be done continuously, comprehensively, and automatically for our customers.
Want to know if you’re affected? Get in touch with us for a free scan of your infrastructure.
Related resources





