Watch the spooky discussion of this report between Paul Asadoorian and Scott Scheferman
The first thing we need to do this month is to pause for a moment and lift up the family, co-workers, and friends of Vitali Kremez, who recently passed away. He was a titan in this industry and worked tirelessly to expose the tactics and identities of the very worst of the worst cyber criminals on the planet. From all of us at Eclypsium and indeed, the entire cybersecurity community, we will miss you tremendously. Know that your legacy will continue and that your shared mission will only be made stronger and more resolute by all of us. Rest in peace.
Whether it’s the Executive Office, the average consumer, or the threat actors, all eyes are on the security of the technology supply chain. Eyes were glued to the TV as people watched the DOJ charge Huawei (and US subsidiaries) in a racketeering and conspiracy case centered around the theft of trade secrets via fraud and deception in order to “misappropriate sophisticated technology from US companies”. Oh, and in helping the DPRK and Iran spy on their citizens, too. The case puts the ICT supply chain front and center. It sets the stage for what is likely to be an all-out global struggle for the west to protect its intellectual property, and indeed the rubber-meets-road security of the development and production operations of our technology providers.
Already the US has started leveraging the 1950’s era FDPR trade law to protect advanced technologies developed in the US from being sold to certain countries. Russian and Chinese interests have both been affected by sanctions and the latest target is China’s advanced supercomputing industry.
Of course, these challenges are not limited to the US. In the UK, there have been long-running concerns over China’s use of technology to shape and influence global affairs. As recent events confirm, China will leverage every possible measure to coerce or steal technology information, even going so far as to offer a quarter million dollars to former UK pilots to better understand how to counter western military aviation.
Thus it is no surprise that the US has proposed a ban on Huawei and ZTE future sales in the US.
Meanwhile, China continues to leverage the broader technology supply chain to further its aims, by exploiting vulnerabilities of the devices that government and critical infrastructure networks rely on. These attacks pose a significant risk to Information Technology Sector organizations (including telecommunications providers), Defense Industrial Base (DIB) Sector organizations, and other critical infrastructure organizations. Devices being targeted include those from F5, Pulse Secure, Citrix, and Cisco, as well as low-cost popular cameras from maker Hikvision found in both IT and OT environments.
Attacks exploiting the devices continue to spiral out of control, and while China-nexus actors got a lot of the spotlight this month, the attacks are being carried out by every ilk of actor with a variety of motives. Keeping blue teams busy this month is a CVSS 9.8 score CVE in FortiOS that attackers from over 40 IP addresses began exploiting in the first three days following its disclosure. The window of time blue teams have to patch such vulnerabilities keeps getting smaller and smaller. Recall the recent F5 vulnerability that was exploited within 5 days of exposure earlier this spring. Actors ranging from the Iranian ISRG to the ransomware group DAIXIN have been exploiting vulnerabilities in Fortinet and other VPN devices throughout the year, targeting healthcare and other critical infrastructure. Meanwhile, QNAP NAS devices continue to be exploited in the wild, with a dozen CVE’s having been exploited in the wild, the latest of which is being used by the DeadBolt ransomware gang to hit thousands of victims.
New research shows how attackers can persist on printers, even surviving reboots and new firmware updates. Device vulnerabilities are being discovered at a cyclical rate, with new approaches and frameworks leveraging fuzzing to quickly iterate every imaginable input an attacker might try. This is in part why we are witnessing such an increase in velocity, scale, scope, and impact of vulnerabilities being discovered. Malicious actors are making quick work of ‘attack chaining’ (combining multiple vulnerabilities on a device in sequence to go from userland to new privileged attack surfaces, for example). Attackers are also discovering ways to abuse “header stomping” methods to exploit the way devices rely on headers to authorize inputs. This applies to both the aforementioned FortiOS and the F5 vulnerabilities. Expect this trend to continue going forward. As our own Nate Warfield points out, “Every vendor with a web UI should be taking a long hard look at whether they use _HTTP HEADERS_ to make trust decisions. Because all the bad actors are looking for this now. ‘Member path traversals?” via this tweet.
Speaking of fuzzing, the technique also applies to finding vulnerabilities in another part of the technology supply chain: the Windows Kernel and the drivers that have direct access to it. Drivers are routinely used by attackers to perform privileged functions or to target the kernel. Lazarus has been using drivers for quite some time now to circumvent kernel protections in order to disable security controls and perform other low-level functions on target hosts. Some of the drivers they leverage are those associated with firmware updating.
A ton of research has gone into this space in order to draw attention to just how broken this control boundary is within Windows. This month, a researcher again leveraged newer fuzzing tools in order to abuse a common Nvidia graphics driver. Yet research in the area of fuzzing the kernel goes back well over a decade, with research by the venerable Richard Johnson in 2017, Eclypsium’s own Screwed Drivers, and even further back in 2011, with attackers able to leverage DirectX to target the kernel. CISA’s list of KEV’s (Known Exploited Vulnerabilities) includes over 25 Windows kernel and 25 driver vulnerabilities, including DirectX drivers targeted as recently as 2018, showing how even seven years after the 2011 research DirectX is still a viable vector for attackers. Put differently, attackers continue to leverage a systemic weakness the entire Windows-related technology supply chain faces: the inability to revoke vulnerable drivers from the list of thousands of drivers Windows trusts. This is both a scope and complexity challenge and one that won’t be solved soon, despite claims that Windows has everything it needs to mitigate the risk, even as actors like Trickbot leveraged the oft-used rweverything driver to gain low-level access to system information. Fast-forward to this month, and we see ransomware groups like BlackByte using a widely used graphics card overclocking utility’s drivers to effectively disable over a thousand other drivers that host security solutions require to function. Much like WinIO.sys (discussed in last month’s threat report, and recently used by Lazarus), the drivers used by BlackByte don’t even require shell code or exploitation; they can simply be sent inputs by the attacker and the commands are carried out at system level. If a Windows device is a battleground, asymmetric driver-based attacks like this are summarily leveling the playing field, time and again. The advantage to the attacker.
Continuing to work our way up the stack from firmware and drivers, there is also no shortage in the abuse of the overall software supply chain. Sonatype recently released research highlighting how modern software supply chain attacks are up over 742% in the last 3 years alone: Tens of thousands of such attacks this year alone, and nearly 100,000 in total so far; and this is just from one source of analysis, and only includes confirmed malicious packages. However, just like with drivers, even software that is not innately malicious can be used for malicious purposes, as any DFIR practitioner will readily and enthusiastically acknowledge. Such is the case, for example, with so-called ‘legitimate RATs’ often abused by actors. This month, Checkmarx discovered a crime group, LofyGang, targeting over 200 packages in the software supply chain, implanting several classes of malicious payloads and password stealers. The campaign has been in operation for over a year and highlights how entire underground communities have been established to specifically target and poison the software supply chain. Not to be outdone, Lazarus has also been caught weaponizing versions of common tools like PuTTY, KiTTY, TightVNC, and well-known PDF Reader.
Even more eye-opening, a group of researchers just discovered that 1 in 10 repositories hosting exploit PoCs (Proof of Concept) has added malicious code in it to target the researcher or red-teamer using the code to validate vulnerable systems on enterprise networks. They looked at over 47,000 such PoCs from the last 6 years, and found 4,893 of them had backdoors, malware, or malicious call-backs.
Against this backdrop of technology supply chain battles, Intel confirmed that the source code for its Alder Lake BIOS was leaked. An email account associated with someone working for a Chinese developer and manufacturer of Lenovo devices originally posted the source code on GitHub (since taken down, but still propagating on other GitHub pages). Initial analysis of the leak indicates there may be sensitive data such as secret MSRs typically reserved for privileged code, and even the private signing keys for Intel’s Boot Guard technology. Other data related to the trusted execution technology central to the root of trust was also found.
Needless to say, this leak may be a boon to attackers of every ilk looking to find backdoors, or develop exploits and tactics associated with targeting the all-important UEFI. Intel has upped the ante of its bug bounty program as its only after-the-fact avenue to help mitigate such risk.
Last month’s report focused heavily on the Energy sector, and for good reason. Attacks haven’t let up, and energy targets are being hit in many regions across the globe. This month, a newer (by name at least) actor group called “Royal”, has begun targeting energy sector victims in Houston and Dallas. Some of these victims would serve as quintessential supply chain targets, with actors potentially gaining access to their solutions that provide operational environment visibility to their downstream customers. Royal commands high ransom amounts ranging up to 1 million dollars and advertises itself as a double extortion type campaign. Many of their tactics, including even the ransom note itself, are very similar to those of Conti. Conti, the same collective that has pledged allegiance and support to the Russian government with ties to the FSB per recent Conti leaks discoveries. The takeaway? Victims should not treat incidents as if the sole motive is profit, and the sole objective is dropping a ransomware payload. Analysts are currently reviewing some of the recently leaked data, hoping to determine what impact the data might have on operational security and downstream operational environments.
Shifting to nation-state-sponsored attacks on the energy sector, Joe Slowik wrote a great analysis covering the many moving parts and organizations that were likely involved in the Trisis/Triton attacks several years ago. The key takeaway is that such threat actors are not single organizations, but multi-faceted, interrelated cogs of a larger set of gears known as XENOTIME, all being driven by command authority. That multitude of actor participants didn’t just ‘stop hacking’ after the 2017 Trisis incident. They remain active, and as Joe posits, the 2017 event might best serve as a preview of what’s to come. An on-point quote in his research is:
“The trend of ‘probing, but not exploiting’ appeared to continue when comments from Dragos in 2022 indicated continued XENOTIME-linked operations against liquefied natural gas (LNG) operations, likely in the US [21]. Although emphasized an initial access and survey operations, the identified activity would represent continued interest by XENOTIME in US critical infrastructure operations, while also aligning with efforts to research but not (immediately) disrupt targeted networks.” – Joe in Zeroing in on XENOTIME: Analysis of the Entities Responsible for the Triton Event
As we often mention here, destructive attacks appear in nature to look like espionage attacks all the way up until the moment the adversary has the political will to turn destructive. This is true at all layers of the infrastructure stack, and undoubtedly true when it comes to destroying critical devices at the firmware/motherboard level, resulting in indefinite downtime that not even resilient backup SOPs can mitigate.
Attacks on the energy sector have not been limited to western targets. Iran’s Atomic Energy Agency was hit by alleged ‘state sponsored’ actors. In India, Tata Power experienced an attack against an ongoing backdrop of cyber challenges associated with protecting their energy infrastructure and threats coming out China earlier this year. The worldwide energy crisis underway will only exasperate cyber attacks in this space.
The final area we will cover is an evolutionary step in the overall threat landscape whereby hacktivism, in the form of both nation-state-induced as well as grass-roots vigilantism, has taken hold across the globe. Put simply, this time last year the industry was debating whether ‘hacking back’ was ethical, effective, and worthwhile for victims of cyber attacks. Fast forward to today, and we’ve gone well past that threshold to yet another one: pro-active offensive hacking by individuals without criminal or profit motives, solely in the name of attacking perceived and real enemy infrastructure, organizations, and individuals. In effect, this has created a meaningful inflection point and has the potential to create escalation pressure well beyond what we’ve already had with APT and criminal motive actors. While APTs may have the capability, they often choose not to execute the final payloads, and to persist for espionage purposes as long as possible until that threshold. But with vigilante hacktivists, the timeline is ‘now’, and the potential for direct and collateral damage to victim organizations and the supply chains they are a part of is tremendous.
CyberKnow has been tracking hacktivism centered around the Russian invasion since the outset in March. At that time, as mentioned in our exhaustive threat report, there were 38 pro-Ukraine and 20 pro-Russian groups already in play. Now, eight months later, there are 42 pro-Russian and 36 pro-Ukraine groups, and six ‘unknown’ affiliation groups actively and overtly attacking their enemy’s critical infrastructure and supply chains. These are only the ‘loudest’ of the groups, but there are many more operating quietly that may never appear in a table like this:
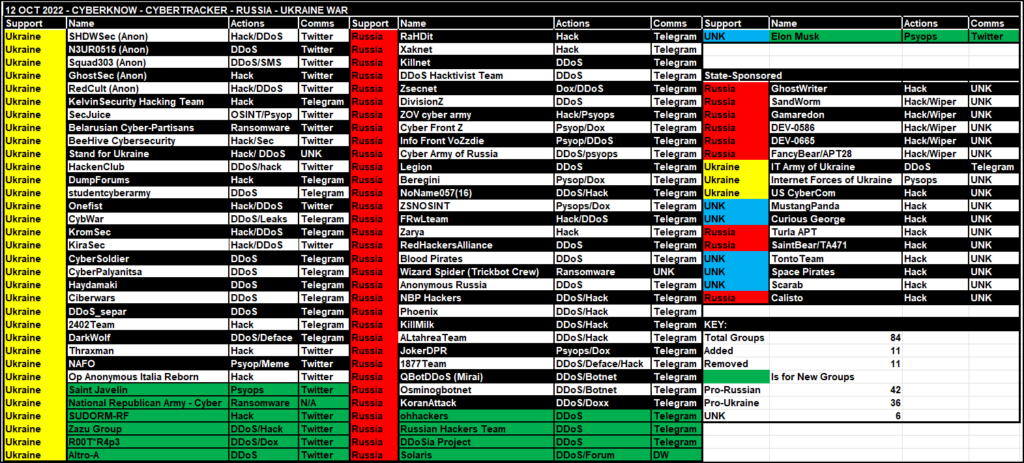
The fallout from the activity of these groups has already been tremendous: Massive dumps of government organizational data, critical infrastructure attacks, targeting of individuals, and the credentials and access to these targets freely available to the expanded threat actor landscape as a result. The objectives range from leaking data to disruption to destruction. Russian government and infrastructure, for example, have never experienced this level of intensity, with groups like XAKNET having gained access to Russian SBU, and even politically motivated actors hoping to topple Putin’s regime (the National Republic Army) having hacked and leaked data of Technoserv and nearly a dozen other companies providing national security and defense contracting services to the Russian government.
In the context of destruction, even the worst of low-level attack tools has been made available to any actor with the will and a small sum of money. This month, a new UEFI bootkit is being offered for only $5,000 USD and comes with all the bells and whistles normally associated with nation-state-level tradecraft. Known as Black Lotus, this offering presents a significant leap ahead for criminal, nation-state, or hacktivist actors (like this pro-Russian actor about to target a Ukraine power provider, or this one about to target a Norwegian weapons supplier to Ukraine, or this Iranian actor targeting NATO in support of Russia). We can only hope (until a sample is found) that the Black Lotus UEFI malware isn’t as fully capable as described, given it performs anti-debugging, anti-virtualization, secure-boot bypass, code obfuscation capabilities, UAC bypassing, and the disabling of Windows Defender, BitLocker, and Hypervisor-protected Code Integrity. If there’s one piece of malware you don’t want in IT or OT environments, it’s Black Lotus:
Considering this tradecraft used to be relegated to APTs like the Russian GRU and APT 41 (China nexus), and considering prior criminal discoveries we’ve made alongside Adv-Int (e.g. Trickbot’s Trickboot module), this represents a bit of a ‘leap’ forward, in terms of ease of use, scalability, accessibility and most importantly, the potential for much more impact in the forms of persistence, evasion and/or destruction.
Prior to this discovery and that of Trickboot, the most advanced cyber criminal malware concern targeting firmware was what we found the Conti group had been researching and developing via the Conti-Leaks (targeting Intel ME in order to write to the SPI Flash). Should criminal actors turn to such kits for more than evasion and persistence, (for example, destroying devices at the UEFI level) they may gain even more leverage in the context of destroying critical assets during a ransomware event, or in the context of disrupting supply chains. The same goes for hacktivists.
To address this now complex threat landscape largely focused on leveraging the dynamics and vulnerabilities of supply chains, the cyber industry has been heavily investing in new startups geared to meet these threats head-on and help us prepare for what is soon to come. Both of the sub-bullets in the headline below say it all: the threat landscape itself, and the new Executive Office Memorandum (heavily discussed in last month’s threat report), are both leading to a new wave of cyber solutions like Eclypsium that are well-suited to help enterprises and missions take on the challenge.
Beyond just cyber vendors, the entire technology supply chain has been put to task, with an incredible amount of effort on the part of OEMs and their upstream providers to specify how to use SBOMs (Software Bill of Materials) throughout the firmware supply chain maze…something Eclypsium has been building into its solutions for Enterprise, Mission and OEMs for some time. While this is still a relatively new capability for all stakeholders involved, suffice it to say, there simply cannot be adequate visibility, actionability, audit, accountability, and notifications without a strong SBOM/FBOM (Firmware Bill of Materials) strategy from all of us.
So, if after reading this month’s report, you start to feel as if supply chain security will be the #1 driver from board members and attackers alike, you aren’t alone. It absolutely will be. From all of us here at Eclypsium, we stand ready to help navigate, frame, and solve this challenge.






